1. The dilemma of the cyber security industry
Digital transformation has spurred tremendous growth in digital resources beyond government and corporate network boundaries, with more applications and data moving to the cloud, and more and more employees needing to access them on multiple devices from anywhere. At the same time, attackers are becoming more sophisticated and cyber-attacks are becoming more advanced, so the traditional security model of building an unbreakable fortress for resources and data cannot meet today's challenges. After more than 20 years of competition between offense and defense, the development of the cyber security industry seems to have reached a very embarrassing dilemma – "As virtue rises one foot, vice rises ten!”. The two sides of the game have entered an endless loop, and the users at stake are tired of this kind of rush to deal with it. This issue is worth pondering in the cyber security industry.
2. Zero trust, the highest state of security
The concept of "Zero Trust" was put forward by John Kindervag, the former chief analyst of Forrester Research in 2010. The core idea is that everyone and things are untrustworthy and need to be constantly verified for its access to any resource. This security concept is widely recognized ten years later. So, zero trust is very hot now!
The US National Institute of Standards and Technology released SP 800-207 "Zero Trust Architecture" in August 2020. The abstract of the guiding standard as follows: Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. A zero trust architecture (ZTA) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned). Authentication and authorization (both subject and device) are discrete functions performed before a session to an enterprise resource is established. Zero trust is a response to enterprise network trends that include remote users, bring your own device (BYOD), and cloud-based assets that are not located within an enterprise-owned network boundary. Zero trust focuses on protecting resources (assets, services, workflows, network accounts, etc.), not network segments, as the network location is no longer seen as the prime component to the security posture of the resource. This document contains an abstract definition of zero trust architecture (ZTA) and gives general deployment models and use cases where zero trust could improve an enterprise’s overall information technology security posture. This document contains the definition of a Zero Trust Architecture (ZTA) and presents a common deployment model and use case for Zero Trust to improve the overall information technology security posture.
Not only that, on May 12, 2021, US President Biden signed Executive Order No. 14028 "Improving the Nation’s Cybersecurity". In this executive order, "Zero Trust" was used 11 times, and the core content was: To keep pace with today’s dynamic and increasingly sophisticated cyber threat environment, the Federal Government must take decisive steps to modernize its approach to cybersecurity, including by increasing the Federal Government’s visibility into threats, while protecting privacy and civil liberties. The Federal Government must adopt security best practices; advance toward Zero Trust Architecture; accelerate movement to secure cloud services, including Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS); centralize and streamline access to cybersecurity data to drive analytics for identifying and managing cybersecurity risks; and invest in both technology and personnel to match these modernization goals. This presidential executive order clarifies that the first best practice for cyber security is to move towards a zero trust architecture, followed by a more detailed explanation of the zero trust architecture. To implement this executive order, the US Office of Management and Budget (OMB) released the "Federal Zero Trust Strategy" on January 26, 2022, requiring US federal government agencies to gradually shift to a security architecture based on zero trust principles.
In China, in September 2019, the Ministry of Industry and Information Technology publicly solicited opinions on the "Promoting the Development of the Cybersecurity Industry (Draft for Comment)", and "Zero Trust Security" was listed for the first time as a key technology that needs to be broken through in cybersecurity. The China Academy of Information and Communications Technology also released the White Paper on China Cyber Security Industry (2019), which for the first time listed zero trust, 5G, cloud security, etc. as China cyber security key sub-field technology. Zero trust security has attracted great attention from relevant government departments and the industry. At present, all cyber security vendors have proposed their own zero trust security solutions, and various related technical conferences are also emerging. Search for "zero trust" can understand its popularity. The reason why zero trust is popular and hot is that it has indeed found an idea to solve the current dilemma of the cyber security industry, so everyone is optimistic about zero trust, and has participated in and proposed various solutions based on this advanced concept.
3. Zero trust security solutions based on cryptographic technology is far-sighted
It is not only that the United States attaches great importance to the zero trust principal and zero trust architecture, in fact, China promulgated the "Cryptography Law" as early as October 26, 2019, and it came into effect on January 1, 2020. The " Cryptography Law" makes it very clear that in order to solve cyber security problems, cryptographic technology must be enforced. As for how to use cryptography, Article 2: “The term "Cryptography" in this Law refers to technologies, products and services that use specific transformation methods to encrypt and protect information and secure authentication." It has been explained very clearly.
Cryptography is the technology, products and services used for information encryption and security authentication. That is to say, the core of the Cryptography Law is zero trust. Cryptography must be used to achieve identity authentication, and cryptography must be used to encrypt information. This is not only the "never trust, always verify" of the zero trust principle, but also "always encrypted", which can be said to be a higher level.
Not only the " Cryptography Law", the "Data Security Law" that took effect on September 1, 2021, and the "Personal Information Protection Law" that took effect on November 1, 2021, both require zero trust security protection for data and personal information. The use of data and personal information with any implied trust is not permitted, and there is a "zero tolerance" for the illegal use of data and personal information, this is zero trust.
Cryptographic technology is the cornerstone of cyber trust technology. It completely solves the four major problems in cyber trust, including the authenticity of the entity's identity, the trust of behavior, the integrity of information, and the confidentiality of information. It is the safest, most effective, most economical and most reliable technology. Cryptographic service is the cornerstone of the cyber trust service, because the cryptographic service realizes the cryptographic application function based on the cryptographic technology and products, supports the cyber trust service to provide services such as identity authentication, authority management, and responsibility determination, and ensures the trust of the cyber identity, data source trusted, content trusted, and cyber behavior trusted.
The best practice of the zero trust principal is the comprehensive application of cryptographic technology and cryptographic services, which not only solves the problem of cyber trust, but also solves the ultimate goal of website security - data security.
4. ZoTrus Technology, cryptographic application automation, innovative solutions to trust and security problems
The founder of ZoTrus Technology has 18 years of experience in cryptographic technology R&D and application and CA operation. The original intention of establishing ZoTrus Technology is still cryptographic application. ZoTrus Technology is positioned as a zero trust security provider based on cryptographic technology, and fully adopts cryptographic technology to realize digital signature and encryption application, because the core technology of cryptography - PKI technology is born to solve the problem of cyber trust and to solve information security.
The core ideas of zero trust security solution of ZoTrus Technology are:
- Never trust unvalidated identity and unencrypted websites.
The website is the first source of information, the identity of the website must pass trusted identity validation, and the transmission of website information must be encrypted to effectively ensure the security of the first biggest traffic on the Internet. - Never trust individuals with unvalidated identities.
Each individual in the network needs to pass identity validation and has a digital certificate to prove its trusted identity. Each network access needs to present a digital certificate to complete the trusted verification. - Never trust cleartext data & messages.
Each data is encrypted with a digital certificate to achieve reliable transmission and reliable data exchange in a zero trust network environment. If the data is not encrypted, it cannot be proved that the data has not been illegally tampered with and illegally leaked. Data & messages include various data, documents, files, emails etc. - Never trust data & messages without digital signatures.
Each data is digitally signed and timestamped with a digital certificate. Only in this way can it be proved that the identity of the data, the time of data generation, the time of use, the data has not been illegally tampered with. Data & messages include various data, documents, files, emails etc.
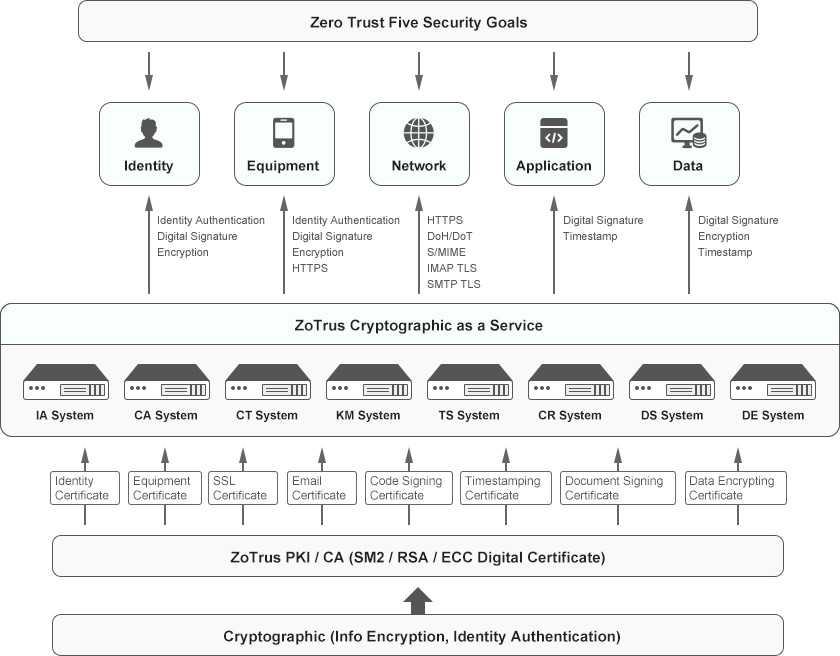
The following figure is a schematic diagram of the implementation of zero trust security technology based on cryptography. The five security goals of Zero Trust are identity trust, device trust, traffic encryption, application trust and data encryption. These five goals can be achieved through the digital signature and encryption of digital certificate. It can be seen that cryptographic technology is the foundation technology of zero trust security.
The core of PKI technology based on cryptography is to issue digital certificates for users, including identity certificate, device certificate, TLS/SSL certificate, email certificate, code signing certificate, document signing certificate, timestamp certificate and data encryption certificate, etc. These certificates can be issued using the SM2 algorithm or the RSA/ECC algorithm according to business needs, ensuring the global trust and national cryptography compliance of the cryptographic applications required by the business.
ZoTrus Cloud Cryptographic Infrastructure is mainly composed of IA System for identity authentication, CA System for issuing digital certificates, CT System for certificate transparency, KM System for managing keys, TS System for timestamping service, CR System for certificate revocation status querying, DS System for digital signature, and DE System for data encryption, these eight systems in cloud effectively ensure the trust of each network element identity and the encryption of each connection, and reliably provide cryptographic services for zero trust security. ZoTrus Cryptography as a Service makes users do not need to invest in the deployment of cryptographic systems, key management systems, timestamp systems, data encryption systems, digital signature systems and identity authentication systems, etc., and only need to use the cloud cryptographic services to archive digital signature, encryption and timestamping services.
Each individual in the network has a trusted identity and has an identity certificate or device certificate. Digital signatures are used to prove their trusted identity. Every time they access network resources, their digital identity (signature verification) needs to be verified. In order to protect the data itself, each data must be encrypted with a certificate and stored in the cloud in ciphertext. Once the user gets the data legally after authentication, he can decrypt it with his identity certificate to get the cleartext data. Whether the data is generated or used, there will be timestamped to ensure that the time of data generation and use is trusted, non-repudiation and non-tampering.
For network traffic security, the most important thing is to use SSL certificates to implement https encryption to ensure the encrypted transmission of all network traffic, whether it is an internal network or an external network, all traffic needs to be encrypted according to the zero trust principles. Based on cloud WAF and CDN services, ZoTrus Website Security Cloud Service automatically configure SM2 SSL certificate and ECC SSL certificate, adaptive cryptography algorithm, fully automatically implement HTTPS encryption with cryptography compliance and global trust. And website security also requires security protection and trusted identity validation, website identity is as important as encryption. The second largest traffic on the Internet is email, all emails also need to use S/MIME technology to achieve end-to-end encryption with email certificates. And the email exchange protocols SMTP and IMAP protocols also use TLS encryption, which not only ensures the email content security in the transmission and in cloud storage, as well as the security of email accounts and passwords. ZoTrus Email Security Cloud Service automatically realizes end-to-end email encryption, it is an email security solution that integrates email encryption, digital signature, and timestamp, which can effectively eliminate email security issues such as email fraud, email leaks, and email identity spoofing, thereby ensuring the security of digital business communications. Another important traffic is DNS resolution. The DNS system must support the encrypted DNS protocol - DoH (DNS-over-HTTPS) or DoT (DNS-over-TLS) and must use the encrypted DNS protocol to communicate with the upper-level DNS system. And all applications (such as web browsers) should also use encrypted DNS services.
For applications (software) security, it is not only necessary to conduct regular security inspections and timely upgrades and patch leaks, but the security foundation is that all application software must have a trusted digital signature, and all software codes must be digitally signed with a code signing certificate and with timestamp signature, which is not only important to protect the security of the operating system, but also is particularly important for Internet of Things device systems that are upgraded over the air. During the over-the-air (OTA) upgrade, it is necessary to verify whether the digital signature of the software is trusted, and whether the timestamp signature is trusted, the upgrade process must be based on zero trust principle, the upgrade software can be installed only after verifying its trusted digital signature in real time. Only in this way can remote attacks by malicious software be prevented. All operating systems and all device systems should strictly abide by the zero trust principle, never not trust software without digital signatures, and only install and run software with trusted digital signature. ZoTrus Application Security Cloud Service is an innovative cloud service that uses digital signature and encryption to ensure the security of application software. It realizes the always verification for the digital signature of application software to ensure that the source of application software is trust, thereby ensuring the security of system and equipment software operation.
For data security, data encryption using encryption certificates is of course the only reliable protection measure. And the digital signature and timestamp signature of the data must be realized by using the signature certificate to ensure that the identity of all data and the time of data generation are trusted. For the use of data, the user can obtain the data only after the user presents his identity certificate and passes the security authentication and encrypts the data with the public key and returns it to the user. Data users must use their identity certificate to digitally sign and timestamp to record data usage behavior and usage time. This is the most important core part of zero trust data security, the purpose of zero trust authentication is to protect the legitimate use of the data. Encrypting data with the public key of a legitimate user ensures that only the authorized user can decrypt the data, which is the most effective data protection mechanism.
It can be seen that the zero trust security realized by ZoTrus Technology using cryptographic technology, the core is the comprehensive application of cryptographic technology automation, which not only solves the problem of trust, but also solves the problem of data security, because the purpose of network protection is to protect data. Encryption using cryptographic technology is the only reliable technology to protect data, and it is also the only technology that complies with the information encryption requirements of the "Cryptographic Law"; and digitally signing data is the only technical means that can prove the trusted the data; data visitors are required to present its digital certificate, which is the only technology that meets the security authentication requirements of the “Cryptography Law”.
We believe that zero trust plus cryptography can only truly solve the current problems faced by cyber security. Cryptography is the protagonist of zero trust security. It is not difficult to understand why IDC predicts that "the transition from the security market to the trust market will become a trend".