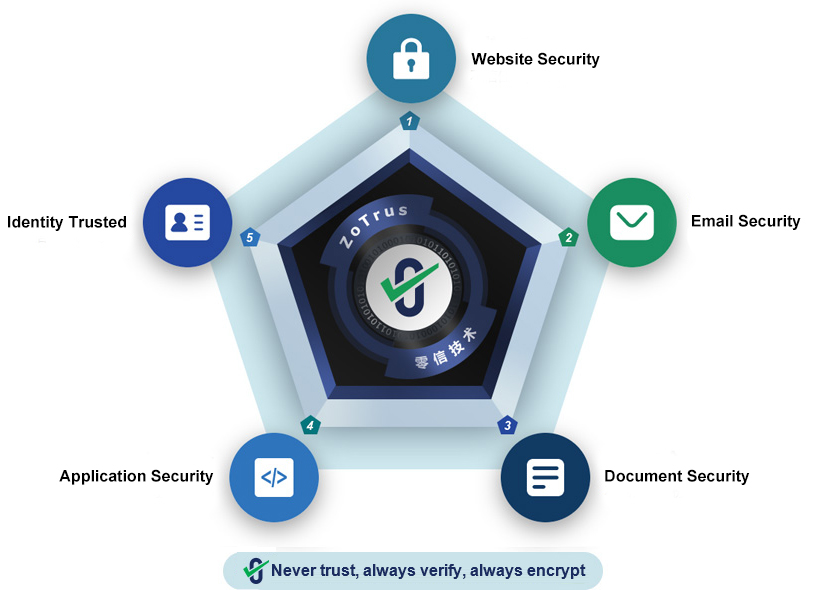
The Three Concepts and Five Principles of ZoTrus
1. Three Concepts of ZoTrus
Never trust
always verify
always encrypt
This is a zero trust security concept formulated by ZoTrus Technology based on the general zero trust concept and cryptographic technology. "Never Trust" is the core concept of zero trust, which is realized by 5 "untrust" cryptographic applications. Our "Always Verify" has a little different meaning with the general term "always verify", because our solution is to always verify the digital signature, users must present a digital identity certificate, and use the identity certificate to sign the authentication information, client software or identity authentication system must verify that the digital signature is valid before it can be passed. The immutable and non-repudiation native trust property of digital signatures is a reliable technology for “always verify”.
“Always Encrypt” is an innovative feature of our Zero Trust security solution. We believe that the purpose of achieving zero trust is to protect data security. We use digital certificate to verify that the identity is not only 100% correct, but also does not require constant screening to ensure an accuracy rate of more than 90% like "Sherlock Holmes". More importantly, we can also use this identity certificate to encrypt the data, so that only people and things who have the right to use this data can decrypt and use it. At the same time, we use this identity certificate to realize the digital signature of the data to prove the trusted identity of the data, so that the data user can securely use the received data. This is a reliable data security protection added to the "Never Trust and Always Verify". It is a zero trust security solution that meets the requirements of the related laws and is the goal of zero trust.
2. Five Principles of ZoTrus
Principle One: Never trust http websites with cleartext transmission
This principle is an important principle to prevent data leakage and online fraud because data leakage and data theft are frequent, and fraudulent websites and counterfeit websites are proliferating. The HTTP protocol is transmitted in cleartext, and it cannot guarantee that confidential information will not be illegally stolen or tampered with. Therefore, according to the concept of zero trust, do not trust http websites that do not deploy SSL certificates, not only the identity of the website is not validated, but also the transmission of website content is in cleartext, all browsers will display http websites as "Not secure". For websites that deploy an SSL certificate, the browser will display the security padlock.
Only https encryption is not enough for website security. If the website does not have any security protection, it cannot guarantee that the website will not be attacked. Do not trust the website without any security protection, but only trust the website protected by the Web Application Firewall (WAF). However, with only https encryption and WAF protection, if the identity of the website is not validated, it is a fraudulent website or a fake website, then the website security is still useless. Never trust unvalidated websites is the overarching principle of zero trust, as all web services originate from websites.
The first principle of ZoTrus is never trust http websites that transmit cleartext, and only trust https encrypted and identity validated websites.
Principle Two: Never trust cleartext emails
This principle is the only effective principle to protect email security, because the cleartext emails are very easy to be illegally stolen and tampered in the transmission, and the sender's email address can also be forged at will, which leads to email frauds and email phishing attacks. The only feasible solution is to adopt the concept of zero trust, never trust cleartext emails, and only trust emails with digital signature and encryption, because only with digital signature can ensure that the email address is true, the sender's identity is trusted, and the content of the email has not been tampered with. And with encryption, you can also ensure that the content of the email will not be illegally stolen.
Always verify the digital signature of emails, this is the only technical means to solve email fraud and email phishing attacks, and zero trust for emails without digital signatures and encryption is the only security protection method. Only trust emails with digital signatures and encryption to keep emails secure from email fraud and phishing attacks.
The second principle of ZoTrus is never trust cleartext emails, but only trust encrypted and digitally signed emails.
Principle Three: Never trust documents without trusted identities
This principle is an effective principle to protect the security of electronic documents. Cleartext documents, especially official documents, cannot prove the trusted identity of documents, and are very easy to be counterfeited. All electronic documents must have digital signatures to prove their trusted identity and prevent being counterfeited and tampered with. Adobe Reader has a mechanism to automatically always verify digital signatures that every time the document is opened, the signature will be automatically verified. This is the zero trust security of electronic documents, always verify the digital signature, only trust the verified document with a trusted digital signature and display the signer's identity information on the first line in Adobe Reader.
This mechanism that always verifies the digital signature of the document is a zero trust security mechanism, which can effectively ensure the security of the document. At the same time, the timestamp signature must be countersigned when the electronic document is digitally signed. This is zero trust in the generation time and publication time of the electronic document. Only the timestamp signature is added, and the timestamp signature is always verified every time the electronic document is used to ensure the time reliability of electronic documents. This is the best practice of zero trust in the generation time of electronic documents, which can effectively ensure the trust of the generation time of electronic documents and the trust of the signing time of electronic contracts.
The third principle of ZoTrus is never trust the electronic documents without trusted identities, and only trust the electronic documents with trusted digital signatures and timestamps.
Principle Four: Never trust applications without trusted identities
This principle is an effective principle for protecting the security of computer systems. Windows has zero trust in software without digital signatures. Because there is no digital signature, it is impossible to prove the identity of the software developer, and it is impossible to guarantee whether the software is malicious software. Of course, having a digital signature doesn't guarantee that it's not malware, so Windows will still further check for malware. Windows provides a SmartScreen reputation accumulation mechanism to give each digitally signed software developer a mechanism to accumulate reputation. If developer want to obtain a trusted reputation immediately, the developer need to use the EV code signing certificate to digitally sign the code, and the signed software will be obtained reputation immediately and installed smoothly.
This mechanism that always verifies the identity of software developers is a zero-trust security mechanism, which can effectively ensure the security of Windows operating systems and other operating systems. This signature verification mechanism is also very suitable for all OTA(Over-The-Air) upgrade software. Only trust the upgrade package with a trusted digital signature can guarantee the device security in the software upgrade. At the same time, to prove that the code signing time is trusted, the timestamp signature must also be countersigned when the code is signed. This is zero trust in the generation time and release time of the software code. Only the timestamp signature is added, and every time it runs, the timestamp signature is always verified to ensure that even if the code signing certificate expires, its code signature can still effectively prove its trusted identity.
The fourth principle of ZoTrus is never trust applications without a trusted identity, but only trust applications with trusted digital signatures and timestamps.
Principle Five: Never trust entities without validated identities
This principle can also be called the "boarding flight principle” because flight safety is very important, so it must be verified by real name before boarding flight. As for the online world, never trust any unvalidated entity identity. Only in this way can we avoid the situation that the "Sherlock Holmes" continuous screening still slips fish through the net, which is not allowed for some applications. Each entity must pass identity validation and obtain a trusted identity certificate to prove his or her trusted identity and can obtain access to data resources by presenting a trusted identity certificate and passing the verification.
Of course, each entity can have multiple identity certificates, and different application scenarios require different levels of identity authentication and use different levels of identity certificates to complete the verification, just like different scenarios in real life need to present different certificates. There are already four different identity validation levels for SSL certificates, and the ZT browser address bar displays different user interfaces to help users identify websites with different validation levels.
After entities (people and things) have trusted digital identity certificates, they have the ability for "native trust", which can be used to prove the trusted identities to achieve identity authentication, and can also be used for digital signatures, data encryption and communication encryption. The most reliable security strategy is to only accept trusted identity connections that meet a certain security policy and reject other untrusted connections and use the recipient's public key encryption to achieve reliable data exchange, which does not require constant real-time screening, high efficiency and 100% precise.
The fifth principle of ZoTrus is never trust the entities without validated identities, and only trust the digital identities of validated entities.
In a word, ZoTrus Technology’s zero trust concepts and principals is based on the concept of zero trust, adopts cryptographic technology, and gives full play to the "native trust" mechanism and "native encryption" mechanism of the PKI (Public Key Infrastructure) to protect Internet security and data security. The three innovative concepts and five innovative principles of ZoTrus Technology are an innovative security practice, which can effectively use the zero trust concept to ensure the security of big data and the security of the Internet of Everything.