1. Cryptography is the cornerstone of zero trust security
What is cryptography? Article 2 of the "China Cryptography Law" has a clear definition: "The term "cryptography" as used in this Law refers to technologies, products and services that use specific transformation methods to encrypt protection and security authenticate for information." This definition is very clear. Cryptography is technologies, products and services for information encryption and security authentication. Of course, this Cryptography means the cipher using SM2/SM2/SM4 algorithm. The zero trust principle is "Never trust, Always verify", emphasizing the need to constantly verify identity, which is one of the important functions of cryptography - "security authentication". ZoTrus Technology zero trust security solution does not use insecure username/password authentication, but use cryptographic technology, to be precise, use PKI digital certificate to achieve strong identity authentication. This is an important core application of cryptography.
Another more important core application of cryptography is "information encryption", which is a more important core part of solving zero trust security - data security, whether it is the "Zero Trust Architecture" formulated by the US National Institute of Standards & Technology or the US Office of Management and Budget (OMB) released the "Federal Zero Trust Strategy", which highly emphasized the application of cryptography/PKI, and emphasized the importance of using cryptographic technology to achieve information encryption, including https encryption and email encryption. This requirement is highly consistent with the second core application requirement of “China Cryptography Law”. Because the purpose of zero trust security is to protect data security.
We can also interpret that the core of the "China Cryptography Law" is also zero trust. Cryptography must be used to achieve identity authentication, cryptography must be used to encrypt information, and cryptography must be used to ensure the security of China core information infrastructure. Therefore, the three concepts of ZoTrus Technology are “Never trust, Always verify, Always encrypt”, full cryptographic implementation to realize always-verify-digital-signature and always- encrypt-information.
2. Introduction to ZoTrus Cryptography as a Service
ZoTrus Cloud Cryptographic Infrastructure is mainly composed of IA System for identity authentication, CA System for issuing digital certificates, CT System for certificate transparency, KM System for managing keys, TS System for timestamping service, CR System for certificate revocation status querying, DS System for digital signature, and DE System for data encryption, these eight systems in cloud effectively ensure the trust of each network element identity and the encryption of each connection, and reliably provide cryptographic services for zero trust security.
The following figure is a schematic diagram of the implementation of zero trust security technology based on cryptographic service. The five security goals of Zero Trust are identity trust, device trust, traffic encryption, application trust and data encryption. These five goals can be achieved through the digital signature and encryption of digital certificate. It can be seen that cryptographic technology is the foundation technology of zero trust security.
Each element in the network has a trusted identity, and the cloud cryptographic service issues a digital certificate for it, and all element uses a digital signature to prove its trusted identity, and each network access will verify its digital identity (digital signature verification). In order to protect the data itself, each data will be encrypted with a certificate and stored in the cloud in ciphertext. After the user has verified his identity and obtained it legally, he can decrypt it with his identity certificate to get the cleartext. As for what identity can access what data, it is formulated by the access policy system, and the identity authentication system allows access to the corresponding data according to the access policy after verifying the digital signature. After the user gets the data, he must also verify the data identity and the data timestamp signature before decrypting it with his private key. The network traffic encryption mainly uses SSL certificate to realize https encryption, DNS encryption and SMTP/IMAP encryption, which can effectively ensure the encryption of network traffic and ensure the base security of zero trust.
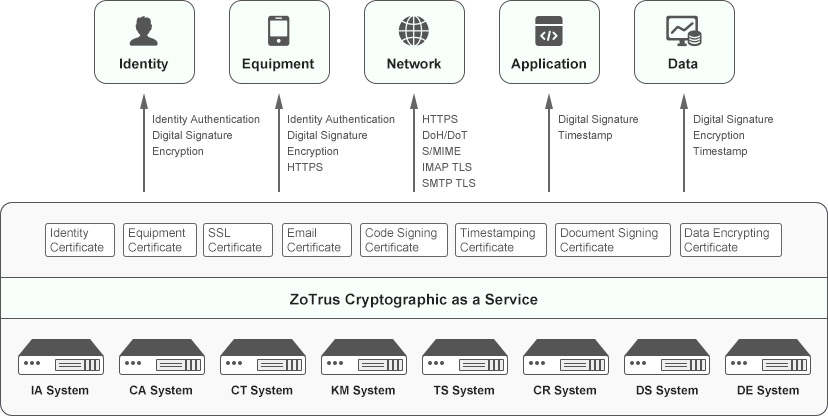
ZoTrus Cryptography as a Service fully supports national algorithm SM2/SM3/SM4 and international algorithm RSA/ECC, users can choose to use SM2 algorithm, RSA algorithm or ECC algorithm to realize digital signature, encryption and timestamp services to ensure the cryptographic application required for business to meet the global trust and national compliance requirement. Customers can choose to deploy an adaptive https encryption service with dual algorithms and dual SSL certificates to ensure that https encryption can be achieved no matter what browser the website visitor uses. For digital signatures, customers can choose dual-algorithm dual-digital signature services, the software system that supports SM2 algorithm verifies the SM2 signature, and the software system that only supports the international algorithm verifies the RSA signature, the timestamp signature also support dual algorithm adaptive. The dual-algorithm adaptive solution can meet the compatibility and compliance requirements.
3. Custom-branded zero trust security issuing CA
In order to adopt the zero trust principle to protect the security of information systems, customers can choose the ZoTrus Cryptography as a Service to automatically issue and deploy digital certificates for management systems. These digital certificates are issued from the ZoTrus issuing CA. For organizations that have higher requirements for certificate security and controllability, it is recommended to customize the issuing CA for zero trust security to consolidate the core infrastructure of zero trust security.
(1) Custom-branded SSL certificate Issuing CA
The first principle of ZoTrus is to encrypt all http traffic and never trust the http website and system that transmitted in cleartext. All website and systems must deploy an SSL certificate for https encryption, ZoTrus HTTPS Automation Cloud Service make the https encryption fully automatic, no need to apply for and install an SSL certificate, no need to install an ACME client software on the server. It can automatically apply for and deploy SSL certificates in the cloud WAF to achieve website https encryption and cloud WAF protection. This is a solution to issue SSL certificates by ZoTrus SSL certificate issuing CA. For important government website systems and cloud service systems, it is recommended to customize your own SSL certificate issuing CA to improve the security level of the business system. Recommended to customize dual algorithm dual SSL issuing CA, one is the SM2 SSL issuing CA for issuing SM2 SSL certificate, which meets the requirements of cryptography compliance, and the other is the ECC SSL issuing CA for issuing ECC SSL certificate to meet the requirements of global trust.
Based on zero trust principle, all websites and business management systems must verify the https encrypted connection every time, and only trust the SSL certificate issued by their own SSL issuing CA, which can effectively prevent https man-in-the-middle attacks. This custom solution is much more flexible and more secure and controllable than verifying a specific SSL certificate each time.
(2) Custom-branded Email Certificate Issuing CA
The second principle of ZoTrus is to encrypt all email traffic and never trust cleartext emails. Not only the web mail login page needs to deploy SSL certificates, but also SMTP and IMAP/POP3 services must deploy SSL certificates, and the most important thing is to implement end-to-end encryption of emails to ensure that emails are encrypted on the way and in the cloud. encryption. ZoTrus Email Security Cloud Service make the email encryption fully automatic, no need to apply for email certificates, no need to exchange public keys in advance, no need to manage keys by themselves, and no need to replace current used email client software, just need to purchase ZoTrus Email Security Cloud Service. This is a solution to issue email certificates by ZoTrus email certificate issuing CA. For important government emails and corporate emails, it is recommended to customize your own email certificate issuing CA to improve the security level of the email system. Recommended to customize dual algorithm dual Email issuing CA, one is the SM2 Email issuing CA for issuing SM2 Email certificate, which meets the requirements of cryptography compliance, and the other is the RSA Email issuing CA for issuing RSA Email certificate to meet the requirements of global trust.
Based on zero trust principle, government email communication and enterprise email communication verify the digital signature of the email every time, and only trust the encrypted and digitally signed email with email certificate issued by the custom-branded email certificate issuing CA, which effectively prevent fake identity emails to keep your email secure. This custom solution is much more flexible and more secure and controllable than verifying a or some specific email certificate each time.
(3) Custom-branded Code Signing Certificate Issuing CA
The third principle of ZoTrus is to digitally sign all application software codes, and never trust software codes without digital signatures. Not only all Windows software requires digital signatures, but more importantly, all OTA air upgrade software must have digital signatures. ZoTrus Application Security Cloud Service make the code signing fully automatic, no need to apply for a code signing certificate, no need to wait for the express USB key hard certificate shipping, no need to manage the signing key, just purchase the ZoTrus Application Security Cloud Service. This is a solution to issue code signing certificates for cloud signing services by ZoTrus code signing issuing CA. For organizations that have important software codes that require digital signatures (such as operating system, security system, smart device manufacturers, etc.), it is recommended to customize their own code signing certificate issuing CA to improve the code signing service security level. Recommended to customize dual algorithm dual code signing issuing CA, one is the SM2 code signing issuing CA for issuing SM2 code signing certificate, which meets the requirements of cryptography compliance, and the other is the RSA code signing issuing CA for issuing RSA code signing certificate to meet the requirements of global trust.
Based on zero trust principle, operating system developers must verify the digital signature of the installed and running code every time, and only trust the code signed by the code signing certificate issued by their own code signing issuing CA to ensure the security of the operating system. The OTA (Over-The-Air) upgrade software of all devices of smart device manufacturers must first verify whether the downloaded software is trusted by whether it has a digital signature and whether it is signed by the code signing certificate issued by its own code signing issuing CA, and only trust the code signed by the code signing certificate issued by its own code signing issuing CA, to ensure that it is an authentic upgrade package and not malicious attack software. This custom solution is much more flexible and more secure and controllable than verifying a specific code signing certificate each time.
(4) Custom-branded Document Signing Certificate Issuing CA
The fourth principle of ZoTrus is to digitally sign all electronic documents, and never trust electronic documents without digital signatures. Whether it is a government electronic document or an enterprise electronic document, there should be a digital signature to ensure that the identity of the document publisher is authentic and trusted. ZoTrus Document Security Cloud Service make the document signing fully automatic, no need to apply for a document signing certificate, no need to wait for the express shipping of USB key, no need to manage the signing key, just purchase the ZoTrus Document Security Cloud Service. This is a solution to issue a document signing certificate for cloud signing services by ZoTrus document signing certificate issuing CA. For government agency and large enterprises (including electronic signature service providers) that have many important documents that require digital signatures, it is recommended to customize your own document signing certificate issuing CA to improve the security level of the document signing service. Recommended to customize dual algorithm dual document signing issuing CA, one is the SM2 document signing issuing CA for issuing SM2 document signing certificate, which meets the requirements of cryptography compliance, and the other is the RSA document signing issuing CA for issuing RSA document signing certificate to meet the requirements of global trust.
Based on zero trust principle, the government and enterprise management systems always verify the digital signatures of all documents every time, and only trust the documents signed by the document signing certificate issued by the custom-branded issuing CA to ensure document security. And inform the user to also check whether the document has a digital signature and the digital signature implemented by the document signing certificate issued by the custom-branded issuing CA. Only in this way can they not be deceived by the fake document. This custom solution is much more flexible and more secure and controllable than verifying a specific document signing certificate each time.
(5) Custom-branded IoT Certificate issuing CA
The fifth principle of ZoTrus is to only trust individuals with trusted digital identities, and never trust individuals with unauthenticated identities. For the Internet of Things, each IoT device must have a trusted identity certificate (device certificate), which represents the unique trusted identity of the device and is used for communication and data exchange between devices and between people and devices. ZoTrus Cloud CA Service and Cloud KM Service automatically distribute keys and automatically issue device certificates for IoT devices. This certificate is issued from ZoTrus IoT certificate issuing CA. For manufactures that have large number of IoT devices that require device certificates, it is recommended to customize their own IoT certificate issuing CA to improve the base security level of IoT devices.
Recommended to customize dual algorithm dual IoT certificate issuing CA, one is the SM2 IoT certificate issuing CA for issuing SM2 IoT certificate, which meets the requirements of cryptography compliance, and the other is the ECC IoT certificate issuing CA for issuing ECC IoT certificate to meet the requirements of global trust.
Based on zero trust principle, issue an IoT device certificate (identity certificate or SSL certificate) to each IoT device to prove identity and encrypt communication, and only trust the communications initiated by devices with identity certificates issued the custom-branded issuing CA to ensure IoT security. This custom solution is much more flexible and more secure and controllable than verifying a specific certificate each time.
4. Localized deployment of ZoTrus Cryptographic Service System
ZoTrus Cryptography as a Service is provided by ZoTrus Cloud Cryptographic Infrastructure, mainly composed of IA System for identity authentication, CA System for issuing digital certificates, KM System for managing keys, TS System for timestamping service, CR System for certificate revocation status querying, DS System for digital signature, and DE System for data encryption, these seven systems in cloud effectively ensure the trust of each network element identity and the encryption of each connection, and reliably provide cryptographic services for zero trust security.
If government agencies and large enterprises have a large number of systems that require self-controllable cryptographic services, they can purchase and locally deploy these sub-systems of ZoTrus Cloud Cryptographic infrastructure according to business need. These systems not only provide cryptographic services, but also can connect to ZoTrus Cryptography as a Service to automatically obtain globally trusted and national compliant digital certificates required for business, and realize digital signature, encryption, and timestamp services for business systems.
5. Advantages analysis of ZoTrus Cryptography as a Service
The founder of ZoTrus Technology has 18 years of experience in CA operation and construction and has a very good cooperative relationship with major national CAs and international CAs, enabling ZoTrus Cryptographic as a Service to automatically configure digital certificates of global trust and national compliance for digital signature and encryption for all cloud cryptographic applications. The founder has persisted in the continuous in-depth research and innovation of cryptographic technology for 18 years, which has ensured the technological leadership of the ZoTrus Cryptographic as a Service.
ZoTrus Cryptographic as a Service has the following ten special advantages:
- Exclusive and "innovative propose that customers do not need digital certificates, but digital signature and encryption services implemented with certificates, and directly provide customers with the required cryptographic services.
- "innovative combine PKI technology with the concept of zero trust, which not only makes identity authentication simpler and more reliable, but also directly protects the data that zero trust security wants to protect.
- The world's exclusive first to realize the website security cloud service integrating https encryption automation, cloud WAF protection automation and website trusted identity validation, providing customers with a full range of website security protection.
- The global exclusive realization of the SM2 Certificate Transparency mechanism, and the SM2 Certificate Transparency log system uses SM2 algorithm to sign the signed certificate timestamp (SCT) for SM2 SSL certificate.
- ZT Browser not only supports the SM2 algorithm and SM2 SSL certificate, but also the world's exclusive to support the SM2 Certificate Transparency, support real time verification of the SCT data in the SM2 SSL certificate, and effectively ensure that the SM2 SSL certificate itself is secure and trust.
- It is the first in China to provide cloud code signing services, which truly solves the pain of customers in using code signing certificates, and provides a practical and innovative solution for popularizing the application zero trust security.
- The cloud signing service automatically identifies file types to be signed, including codes and PDF documents, and realizes one-click automatic digital signature of all types of files.
- The world's first and exclusive email security cloud service using S/MIME standard technology, users do not need to replace the commonly used email client software, or even do not use the email client software, and exclusively support the Web mode to view encrypted emails and send the encrypted email in web, fully automatically provide users with end-to-end email encryption services such as exchanging public keys, key management, encrypting emails and decrypting emails.
- Provide professional custom-branded issuing CA services. The RSA/ECC algorithm customized issuing CA is issued from the world-renowned CA-Sectigo root certificate and supports all browsers, servers, and email client software. The SM2 algorithm customized issuing CA is issued from the ZoTrus SM2 root certificate and supports ZT Browser and other client software. It greatly reduces the cost of CA agencies or certificate agencies without publicly trusted and cryptography compliance root CA but can issue their own brand digital certificate of global trusted and cryptography compliance, and greatly shortens the time to enter the cryptographic application market.
- Unified certificate management interface manages all certificates in the whole life cycle, all in-use certificates, pending renewal certificates and expired certificates can be seen at a glance, completely solved from manual management of manual application and management of certificates, and solved the challenges of missing certificate renewal.
ZoTrus Cryptography as a Service is the cornerstone of zero trust security, only the comprehensive application of cryptographic technology and services can truly implement reliable zero trust security. With ZoTrus Cryptography as a Service, you can easily achieve:
- Based on zero trust principles, only trust the digital certificates that are publicly trusted and cryptography compliance, and never trust the digital certificates that require users to manually install root certificates, thereby effectively preventing root certificate fraud and digital certificate man-in-the-middle attacks.
- Based on zero trust principles, business management systems must verify https encrypted connections every time, and only trust SSL certificates trusted by browsers or operating systems. For important business systems, only trust SSL certificates issued by a specific SSL issuing CA certificate, to prevent the https man-in-the-middle attack.
- Based on zero trust principles, government email or corporate email communication must verify the digital signature of the email every time, only trust the email with digital signature that signed by the email certificate trusted by the email client. For important emails, only trust email certificates issued by a special issuing CA certificate, to ensure the safety of email and eliminate email fraud.
- Based on zero trust principles, operating system manufacturers and equipment system manufacturers must verify the digital signatures of the software code installed and running for each time, and only trust the software code with digital signature that signed by the code signing certificate trusted by operation system and equipment system. For important system software, only trust code signing certificate issued by a special issuing CA certificate, to ensure the security of the operating system and equipment system.
- Based on zero trust principles, all management systems and OA system must verify the digital signature of the document each time, only trust the document signing certificates issued by some specific issuing CA to ensure document security and trust.
- Based on zero trust principles, the Internet of Things equipment must use the device certificate to prove its trusted identity and encrypted communication, only rust the equipment communication that have a certain identity certificate issued by some specific issuing CA to ensure the security of the Internet of Things.